DroidKungFu Malware Evolves Again, Becomes More Difficult To Detect

DroidKungFu is continuing to evolve, with researchers detecting a new generation of the Android malware that incorporates new mechanisms to mask it from users and security software. This is the third version of DroidKungFu to be identified in the past two months.
Like the previous generations of DroidKungFu, the latest iteration takes advantage of two vulnerabilities in the platform software of Android versions 2.2 (Froyo) and earlier to install a backdoor that gives hackers full control of your phone. This provides access to user data, and more importantly allows hackers to turn the phone into a bot – which means they can make your smartphone do anything they want. But the third generation has several new tricks up its sleeve.
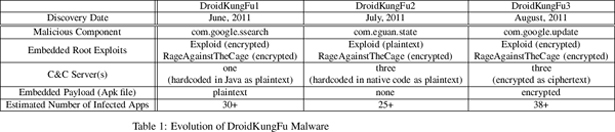
Previous versions of DroidKungFu retrieved instructions from a remote “command and control” (C&C) server, but stored the URL for the server in plain text. This allowed security programs to identify and block the server. DroidKungFu version 3.0 encrypts the C&C URLs, making it more difficult to identify and block them. The new version also encrypts all of the code related to exploiting vulnerabilities has been encrypted, making it harder to identify the malware – until it actually begins operating.
In addition, when DroidKungFu version 3.0 installs its embedded payload (the program that turns your phone into a bot), it masks the program as an official Google update. This keeps phone users from becoming alarmed, and makes it harder to find the program once a problem has been detected.
The new version of DroidKungFu was found by Xuxian Jiang, and his research team at NC State, in over 38 apps available in alternative Chinese markets. A full technical write-up can be found here.
Jiang identified the first version of DroidKungFu in early June, and the second generation less than a month later. The table below shows how the malware has evolved so far.
- Categories: